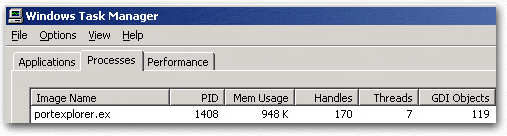
Under the PID column we can clearly see that in this instance the process ID of Port Explorer is 1408. Now that we know the ID of the process, we can tell Socket Spy to start capturing.
Example 2: Capturing all sent
and received data from a process
Right-clicking on a socket in the main Port Explorer window is the most common way to spy on a process/socket, but what if the process you want to spy on hasn't opened any sockets? There's an easy workaround - just manually add the process ID to the spy list! This example will show you how.
To spy on a process, all you need to know is its process ID (PID) - a unique identification number that allows us to specify the exact process we want to spy on. In this example, we'll use Socket Spy to spy on Port Explorer itself (portexplorer.exe), but it could just as easily be any other process.
Finding the process ID is very easy, all you need is a process list utility. For
Windows NT/2000/XP users - simply press Ctrl+Alt+Delete to launch Windows Task
Manager. You'll see Port Explorer in the list as "portexplorer.ex"
(Task Manager restricts the filename size to 15 characters - most other process
lists do not have this restriction):

Under the PID column we can clearly see that in this instance the process ID of
Port Explorer is 1408. Now that we know the ID of the process, we can tell
Socket Spy to start capturing.
Launch Port Explorer if it isn't already started, go to the Utilities
menu, then click on Socket Spy. In the small
textbox just above the Add PID button, enter the
process ID (1408 in this case), and then press the Add PID
button:
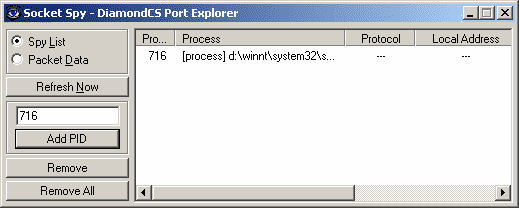
That's all you need to do. Port Explorer will now capture all sent and received data from all sockets owned by process 1408. To invoke Port Explorer to send data, try using the Whois utility.
To view captured packets simply press the Packet Data radio
option. To stop spying on the process, select the process in the list and press
the Remove button.